OverTheWire: Bandit Walkthrough
This post is a WORK IN PROGRESS. Come back later to see more and more as we unlock the mysteries of OverTheWire. Specifically Bandit.
Welcome to my OverTheWire guide! This is a good exercise for learning basic terminal commands. Follow along and come back here if you get stuck. I'll start from level 0 and work my way up.
Level 0:
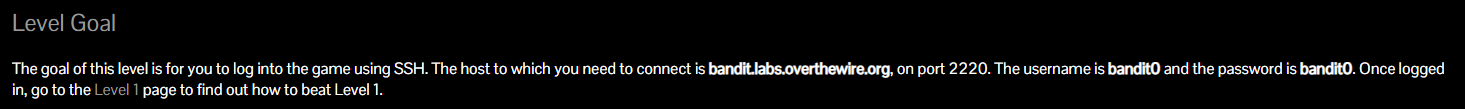
Okay so we need to ssh into bandit.labs.overthewire.org on port 2220 using the user bandit0 and the password of bandit0.
so, open a terminal of your choice and type
ssh bandit0@bandit.labs.overthewire.org -p 2220
log in with the password bandit0 and you're in.
Let's move onto Level 0 -> Level 1:
Back to our terminal, let's look in our current directory
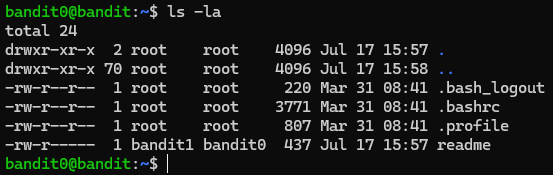
Okay, so we see the readme file. Let's try reading it. Cat is a way to concatenate files and print them out.
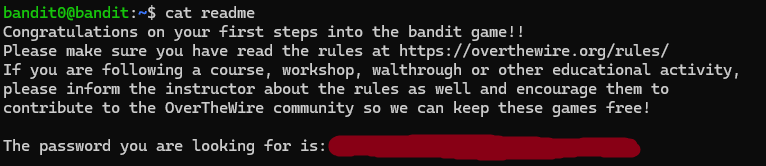
Password acquired.
Level 1 -> Level 2
Exit out of your ssh session (type exit) and now ssh into bandit1@bandit.labs.overthewire.org

This will happen every level. So, keep that in mind if you're looking for a file that just doesn't seem to be there. You might not be logged in as the right user.

Okay, so ls gives us a file named '-'. This can cause us issues because how can we tell our terminal we want the file named '-' and not an argument starting with '-'?
Well, let's give it some context. Just give it the directory and the name. Like /home/bandit1/-, or ./- since ./ means the current directory.
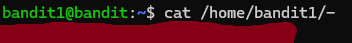
Boom! Let's use that password and get to level 2.
Level 2 -> Level 3
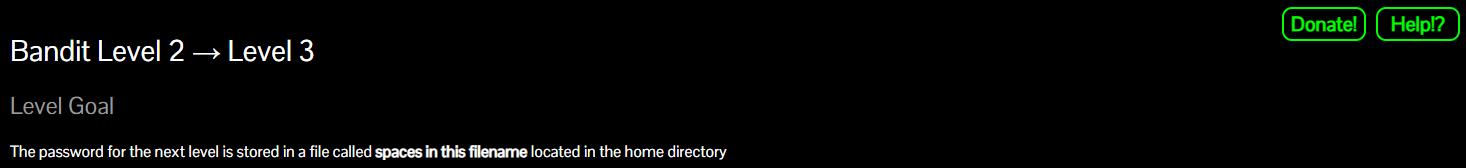
Okay, now the password is in 'spaces in this filename'. Cool. We can just escape each space with a backslash. It will look like 'spaces\ in\ this\ filename'. Or, since we live in the 21st century, we can just type 's' and hit the tab key. That will autofill in the rest of the name. Try this on everything. It's a life and time saver.
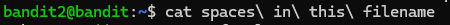
Password acquired. Onto the next level.
Level 3 -> Level 4

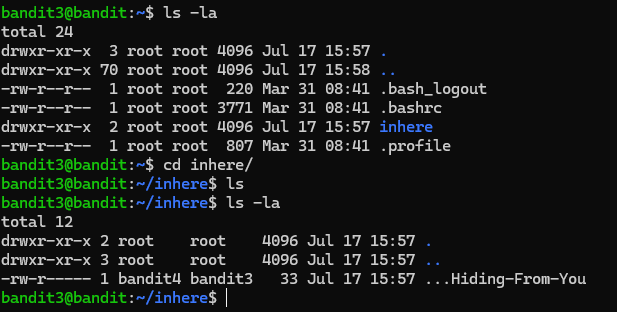
Okay, so we see the inhere folder. We can change our directory there with cd. Now we can type ls -la to list files in a long list all of the files present.
Now we can type cat ...Hiding-From-You and see the next password. (Don't forget about your friend Tab!)
Level 4 -> Level 5
Okay so we cd to the 'inhere' directory and see 10 files, labelled '-file00' to '-file09'.
The goal specifies "human-readable". Let's try using file to see what types of data we can see.
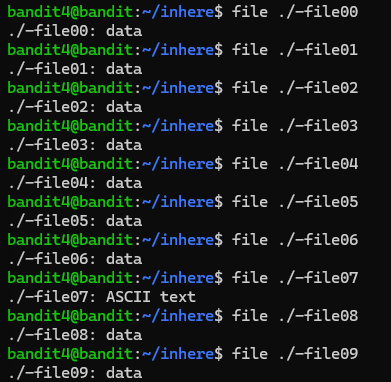
Well look at that. We can cat the outstanding file and we have our password.